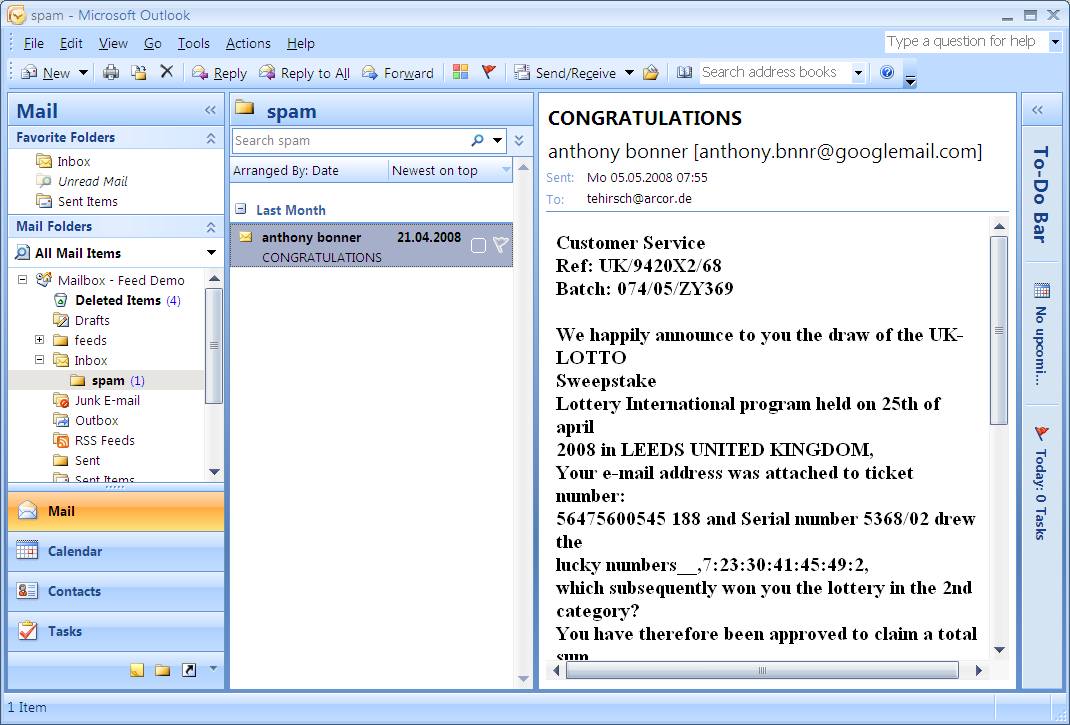
TB/TB-2008-04-CTASAV
TB -> TB/TB-2016-10-CTASAV
Contents
- 1 Overview
- 2 How to setup Scalix AntiSpam and Scalix ZeroHour AntiVirus
- 3 Operations
- 3.1 Impact on incoming mails
- 3.2 How Scalix AntiSpam and Scalix ZeroHour AntiVirus alter your mails
- 3.3 How to report a false negative/positive
- 3.4 How to manually report a false negative/positive
- 3.5 How to test scan a message
- 3.6 Considerations when running a non Scalix mail relay in front of the scanning server
- 4 Client Setup
- 5 Customize Scalix AntiSpam and Scalix ZeroHour AntiVirus
- 6 Troubleshooting
- 6.1 Known Issues
- 6.2 How do I determine if I have a valid license
- 6.3 Checking that the submission port is open
- 6.4 Test that the submission port is used for SWA/Platform/SSMTP
- 6.5 How do I check if mails are (not) scanned
- 6.6 I can not see the sxmilter service
- 6.7 Checking that sxmilter is running
- 6.8 New audit events
- 6.9 Where to find log files
- 6.10 Received: header logging
- 6.11 omshowlog shows "MILTER: milter_eomActions: mkstemp failed"
- 7 Implementation Details
Overview
Scalix AntiSpam and Scalix ZeroHour AntiVirus are two integrated product options which provide the respective protection for your systems. Both are based on OEM technology powered by Cyren's reliable anti-spam, Zero-Hour virus outbreak protection . They are separately licensed products and available for commercial customers running either Scalix Small Business, Enterprise or Hosted edition. Please contact your sales representative if you are interested in one or both of them.
How to setup Scalix AntiSpam and Scalix ZeroHour AntiVirus
To be able to use Scalix AntiSpam and Scalix ZeroHour AntiVirus you will need to perform the following steps:
- Use a Scalix AntiSpam and/or ZeroHour AntiVirus enabled license
- Split inbound and outbound mail traffic
- Enable content scanning
- Restart services to activate configuration changes
- Customize AntiSpam and AntiVirus behaviour
Use a Scalix AntiSpam and/or ZeroHour AntiVirus enabled license
Please refer to How do I determine if I have a valid license on how to check that the license you are using includes support for Scalix AntiSpam and/or Scalix ZeroHour AntiVirus.
File Locations
All file locations that are mentioned below are formated like this:
~/webmail/swa.properties
The ~/ part refers to your mailnode directory, e.g.
/var/opt/scalix/do
So the absolute path of the above file is:
/var/opt/scalix/do/webmail/swa.properties
Split inbound and outbound mail traffic
In the default setup traffic passing the relay is a mix between inbound, outbound and internal mails. To lower the risks of false positives it is recommended to setup Scalix to not scan internal and outbound mail. For that you will need to:
- Enable Submission Port
- Change Scalix Web Access to use the new submission port
- Change Platform to use the new submission port
In case you are using IMAP clients you will also need to implement one of the following possibilities:
- Alter SSMTP stunnel setup
- Alter IMAP client settings
Scalix recommends that you setup stunnel to provide SSMTP and configure your IMAP clients to use this encrypted communications channel.
Enable Submission Port
To enable the Relay's submission port apply the following changes to ~/sys/smtpd.cfg.
Enable submission master switch:
# Uncomment the following lines to enable the Submission and LMTP listeners SUBMIT=ON
Multi server setup considerations
Please be advised that when running a multi server setup all participating servers must have their submission ports enabled and must use the same port. Running a mixed setup where some servers have the submission port enabled and some not or when servers use different ports may lead to problems when sending mail.
Change Scalix Web Access to use the new submission port
To configure SWA to use the new port you need to alter ~/webmail/swa.properties:
#swa.email.smtpServer=demo.scalix.com swa.email.smtpServer=demo.scalix.com:587
Change Platform to use the new submission port
To configure the platform to use the new port please alter ~/platform/platform.properties:
# # SMTP submission port # #smtp.port=25 smtp.port=587
In case you changed the default setting and specified an IP adress in ~/sys/smtpd.cfg for the submit port to bind to, you will need to make sure that the same IP is used in ~/platform/platform.properties for the smtpd.host property:
# # SMTP submission host # smtp.host=demo.scalix.com
Alter SSMTP stunnel setup (optional)
If you are using stunnel to provide SSMTP for other clients like Thunderbird you will need to change your stunnel configuration to also use the submission port. It is typically found under /etc/stunnel/stunnel.conf:
[ssmtp] accept = 465 connect = 587
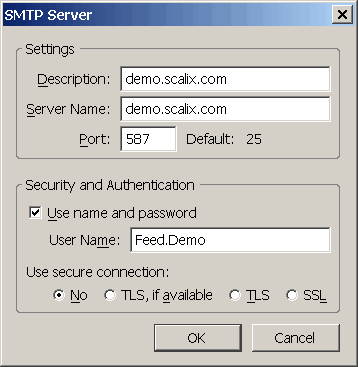
Alter SMTP Client settings (optional)
If you are not using stunnel to provide SSL encrypted SMTP to clients like Thunderbird you will need to alter your clients configuration to also send mail via the submission port.
For Thunderbird this option can be found under Account Settings/Outgoing Server:
How to enable content scanning
To enable MILTER support you need to change the MILTER master switch in ~/sys/smptd.cfg to TRUE:
# master switch to enable milter support (default off) SMTPMILTER=TRUE
and uncomment the Commtouch milter definition:
# list of milters to call sequentially (default none)
INPUT_MAIL_FILTER=('CTmilter', 'S=local:~/temp/CTmilter_socket, F=T, T=C:300s;S:10s;R:10s;E:300s')
Restart Services
To enable the submission port and milter support you will need to restart the relay. To immediately restart it use:
$ omoff -d 0 "SMTP Relay" Disabling 1 subsystem(s). $ omon "SMTP Relay" Enabling 1 subsystem(s).
To activate the changes made to SWA and the platform you will need to restart scalix-tomcat. To immediately restart it use:
$ /etc/init.d/scalix-tomcat restart
In case you changed your stunnel setup you will also need to restart stunnel.
Operations
Impact on incoming mails
Activating Scalix AntiSpam and Scalix ZeroHour AntiVirus will influence the way incoming mails are handled. The following two sections give a high level overview on how Cyren detects Spam and Viruses and how the default configuration impacts your incoming messages.
How Cyren works
When mails are scanned they are classified by Cyren as being of one of the following levels:
| Level | AntiSpam | AntiVirus |
|---|---|---|
| 0 | definitely no Spam | definitely no Virus |
| 1 | no Spam | no Virus |
| 2 | probably no Spam | probably no Virus |
| 3 | probably Spam | probably Virus |
| 4 | confirmed Spam | confirmed Virus |
Based on this classification you then decide what to do with this message:
| Action | Description |
|---|---|
| Accept | Deliver the mail to it's recipients |
| Reject | Reject message (generates error on sending side) |
| Discard | Accept message but silently drop it |
| Tempfail | Temporary fail the message and let the sending side try again later |
The default action is to accept a message, so when no action is defined for a specific level it will get accepted.
Please be advised that depending on the laws in your country you may actually not be allow to silently discard messages, but must reject them if you do not want to accept them. In Germany for example you are not allowed to discard messages, because you are legally bound to deliver mails once you accept them.
If you decide to accept a message you can then apply the following options to it:
| Action | Description |
|---|---|
| Header | Add, delete or change a header. For example add a header to mark this message as spam. The default configuration will add a header to all Level 3 Spam messages to allow users to sort mails using their client, see Client setup. |
| Recipient | Add or delete a recipient. For example to collect all spam massages in a system wide spam account. |
Regardless of the action you choose to apply to a message you can always save it to a file on disk for later inspection. An example on how to do this is given below in the section Antivirus Examples
Default configuration
The configuration shipped with Scalix 12.6 will:
- Accept messages with Spam Levels 0, 1 and 2 (definitely no spam, no spam and probably no spam)
- Accept messages with Spam Level 3 (probably spam), but add headers allowing users to filter these messages using their client
- Discard messages with Spam Level 4 (spam)
- Accept messages with Virus Level 0, 1 and 2 (definitely no virus, no virus and probably no virus)
- Tempfail messages with Virus level 3 (probably virus)
- Reject messages with Virus Level 4 (virus)
How Scalix AntiSpam and Scalix ZeroHour AntiVirus alter your mails
Depending on your configuration Scalix AntiSpam and Scalix ZeroHour AntiVirus will edit, delete or add headers. The RefID header will always be added, per default it is called: X-SMP-CT-RefID.
The following is an example of a message categorized as Spam Level 3 running the default 11.4 configuration:
... User-Agent: Thunderbird 2.0.0.12 (Windows/20080213) X-SMP-CT-RefID: str=0001.0A0B0209.481B49A5.00AD,ss=1,fgs=0 X-Spam-Flag: Yes X-Spam-Level: *** X-Spam-Status: Yes, score=3 required=3 tests=Commtouch ...
This RefID Header is used to identify a message, used for example when reporting back false negatives or false positives.
How to report a false negative/positive
Through the sxmilter tool you are able to report false negatives and false positives. For this to work properly the message you want to report will need to contain a valid Cyren RefID header.
To report a false negative spam message use
$ sxmilter -c 1 -N /tmp/this.was.really.spam.txt
Before sending the report back to Cyren sxmilter will rescan the message to check if it is still wrongly categorized.
In case of a false negative sxmilter will report the mail back as wrongly categorized when the detected level is 0, 1, 2 or 3.
False positives will be reported back for levels 3 and 4.
Please note that passing the -c option to select the category is mandatory when reporting back false negatives/positives. Refer to sxmilter's man page for more details.
How to manually report a false negative/positive
When sending filtered messages to Cyren for analysis, it is important to note that the original messages must be attached to your email report rather than forwarded to Cyren. This is to ensure that all the original message-headers are also sent to Cyren for analysis. Reports that do not contain the original message-headers cannot be analyzed.
Spam classification errors should be reported to the following addresses:
- False Negative to reportfn@blockspam.biz
- False Positive to reportfp@blockspam.biz
Virus classification errors should be reported to the following addresses:
- False Negative to reportfn@vodlab.biz
- False Positive to reportfp@vodlab.biz
Cyren is unable to analyze old messages because spam characteristics are dynamically changing over short periods of time due to the nature of spam distribution methods. It is therefore, very important that you send reports about classification mistakes as soon as possible. In general, you should avoid sending reports that are older than one week.
How to test scan a message
You can use the sxmilter tool to perform test scans on messages. To check a message for SPAM and VIRUS classification use:
$ sxmilter -c 3 -T /tmp/example.message.txt spamLevel=1 CSDKMain_ClassifyMessage antispam completed. virusLevel=1 CSDKMain_ClassifyMessage antivirus completed.
The scanned example message contained in /tmp/example.message.txt scored 1 for both SPAM and VIRUS test.
The following test shows a message being classified as spam
$ sxmilter -c 1 -T /tmp/spam.txt spamLevel=4 CSDKMain_ClassifyMessage antispam completed.
Please refer to the to man page of sxmilter for more information.
Please make sure that the file you are trying to scan is readable by user scalix, else the test run will fail with a non zero exit code.
Considerations when running a non Scalix mail relay in front of the scanning server
Scalix AntiSpam and ZeroHour AnitVirus detection algorithm relies heavily on the IP used when connecting to the Scalix Server.
If you have a non Scalix relay in place in front of the Scalix system running the detection software you will see very poor detection rates as the IP of the relay is used when analyzing incoming mails.
With Scalix 12 two configuration options have been added to allow you to ignore certain ip addresses when scanning for Spam or Viruses and to use the real sending IP. Note that these options are not available in the Scalix AntiSpam and AntiVirus ZeroHour module in 11.4.0 and 11.4.1. You will need to upgrade to 11.4.2 to be able to use this improvement.
How it works
When receiving a new mail the SMTP Relay will scan all Received: headers. It will look for the first IP address not matching MILTER_IGNORE_IP_SENDER and pass this one on to the milter.
The way Received: headers are scanned is configurable through the MILTER_IGNORE_IP_HEADER option and can per default handle the most commonly used formats. The Relay will try them in order they are listed and use the first configuration that produces a valid IP address. In case no configuration matches it will fall back to the IP used to connect to it.
You can specify up to 99 MILTER_IGNORE_IP_SENDER and MILTER_IGNORE_IP_HEADER stanzas each.
Example Setup
Consider the following setup:
- Internet Relay running Postfix, external IP: 1.2.3.4, internal IP 10.0.0.1
- Scalix system running AntiVirus and ZeroHour AntiSpam: internal IP 10.0.0.2
External mail is received by the Internet Relay (1.2.3.4) and routed via 10.0.0.1 to the Scalix system (10.0.0.2). That way the Scalix system would see 10.0.0.1 as the connecting IP.
Configure IP ignoring
Edit ~/sys/smtpd.cfg and set MILTER_IGNORE_IP_SENDER to the internal IP of the external relay:
MILTER_IGNORE_IP_SENDER=10.0.0.1
Note that MILTER_IGNORE_IP_SENDER also accepts a wild card. To ignore all Received: headers from the 10.0.0.0/24 subnet use:
MILTER_IGNORE_IP_SENDER=10.0.0.*
Restart the relay to activate your change.
Alter Received: header matching
In case the provided header scanning configurations need to be changed, you can do so by specifying one or more MILTER_IGNORE_IP_HEADER stanzas.
If for example you also need to parse headers in the form of:
Received: from domain with Postfix (host <IP>)
you would need this additional configuration:
MILTER_IGNORE_IP_HEADER=Received: from %s %s %s %s %s
You can use up to 5 occurrences of %s. Note that the last %s must always match the IP address.
Make sure to uncomment the defaults in smtpd.cfg and to add your configuration as the defaults will not be used as soon as you add one MILTER_IGNORE_IP_HEADER line.
Client Setup
The following sections describe how to setup different clients to use the added headers. All examples assume that you are using the default configuration.
Outlook 2010
Select Rules and Alerts from the Tools menu:
Click on New:
Enter a name for the rule, for example probable spam:
Click on Conditions and select with specific words in the message header:
then click on the specific words link and enter
X-Spam-Level: ***
and select Add:
and Ok. Think link should now have become X-Spam-Level: ***:
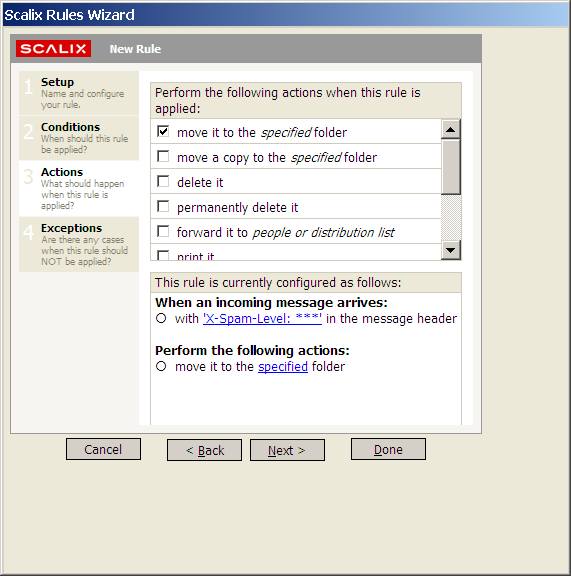
Click on Actions, select move it to the specified folder and click on the specified link:
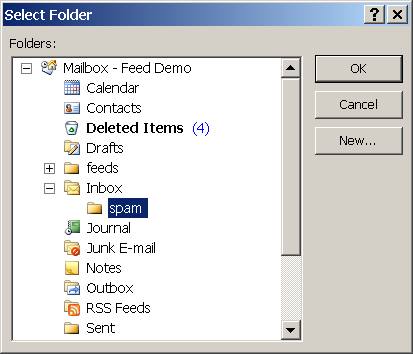
and select your spam folder. If you have not yet created your spam folder you can now click on New to do so:
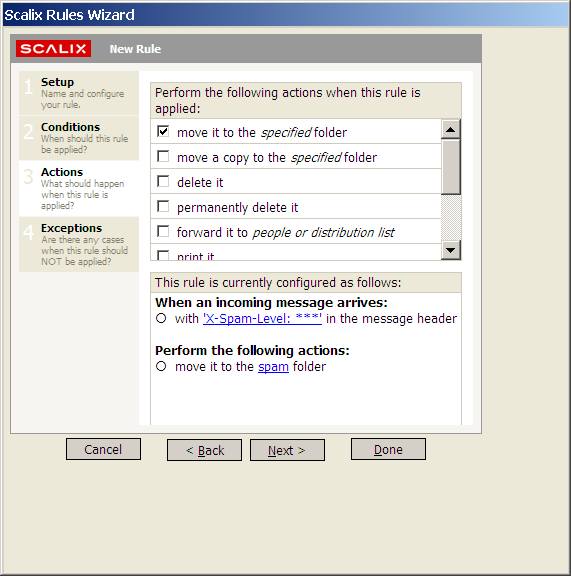
and click OK. The link should now have changed to the name of the folder you selected, in case of this example spam:
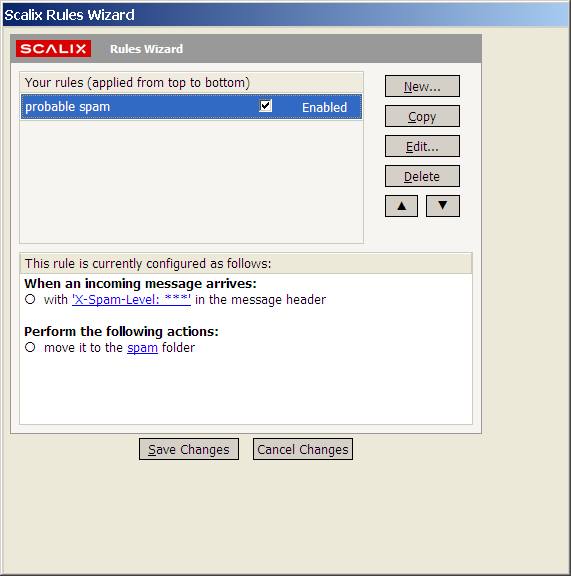
Select Done. You should now have a probable spam rule:
Click on Save changes and new spam will be moved to your spam folder:
Scalix Web Access
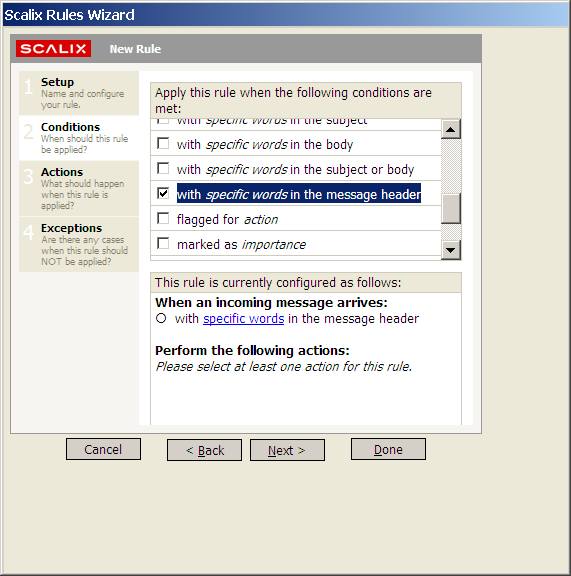
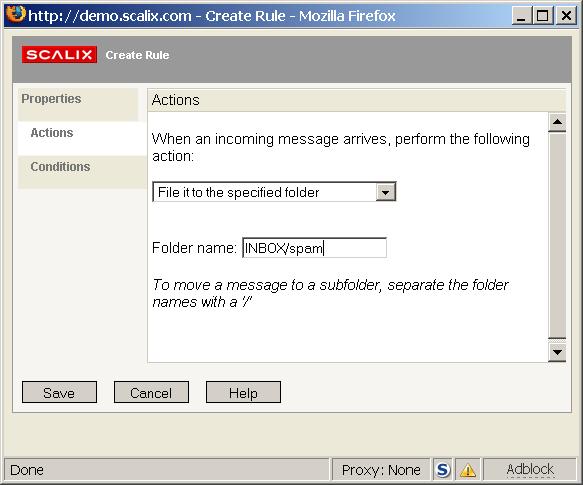
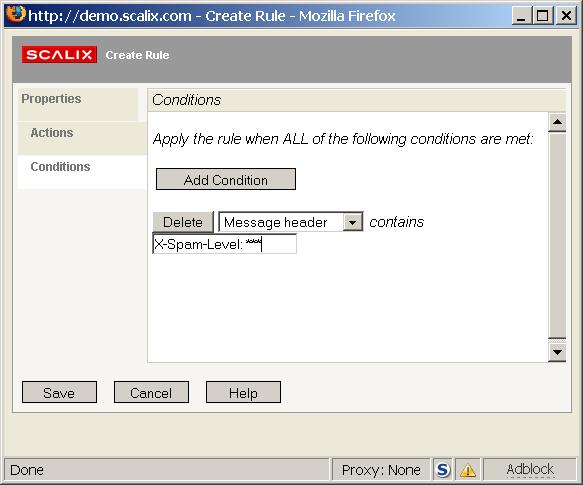
To move all messages tagged as spam to the folder INBOX/spam follow these steps:
Start the Rules Wizard from the Tools menu
Select Create a new rule
Enter a name for the new rule, for example "probably spam"
Select the Actions pane, then select File it to the specified folder from the drop down list and enter a folder where spam mails should be saved, for example "INBOX/spam"
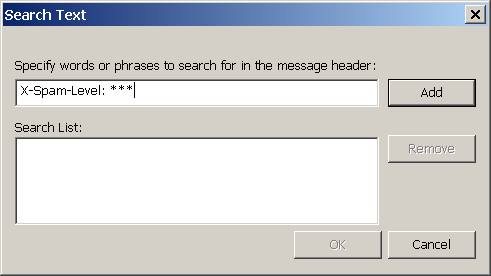
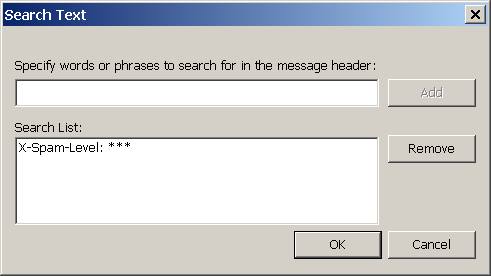
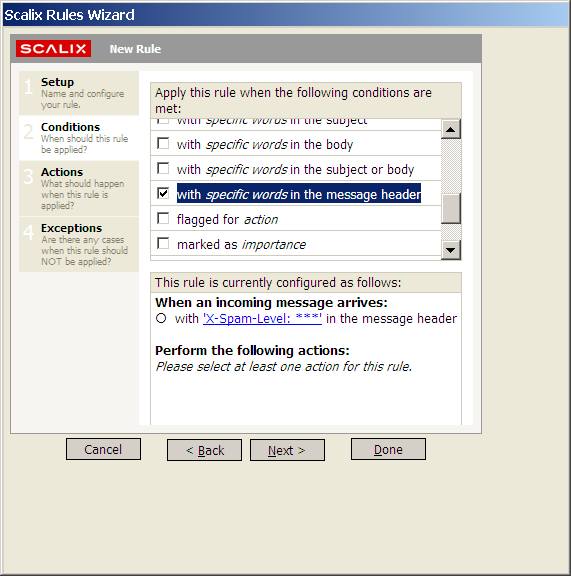
Select the Conditions pane, select Message header from the drop down list and enter
X-Spam-Level: ***
as condition
Click on Save and close the Rules Wizard.
Now when a Spam Level 3 categorized message arrives it will be moved to the spam folder
Thunderbird
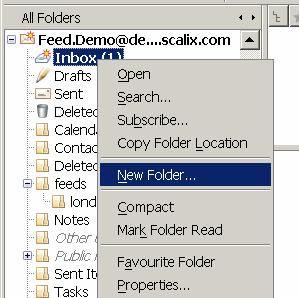
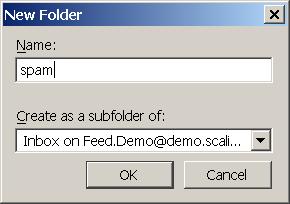
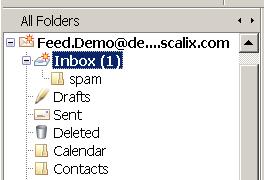
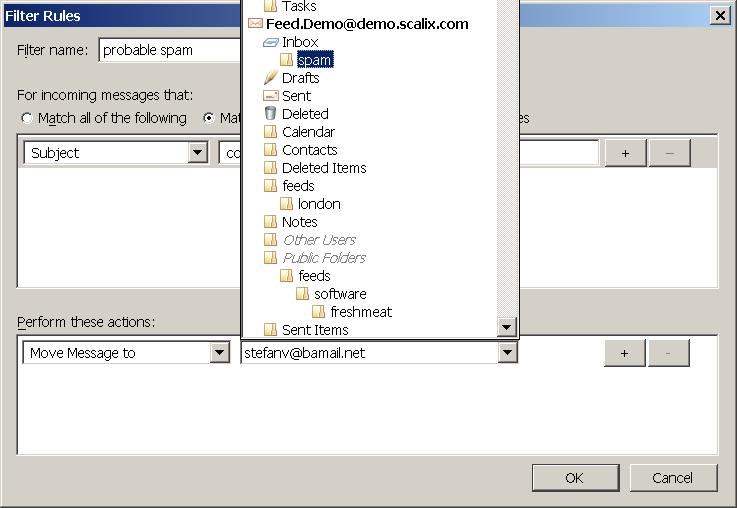
If you have not already done so create a folder where spam mails should be collected. Right click on your INBOX and select New Folder:
Enter a name for the new folder, for example spam:
and select Ok:
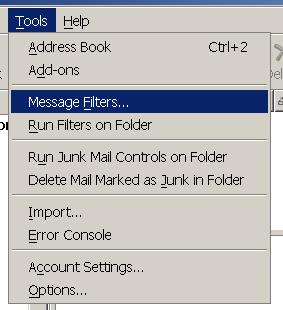
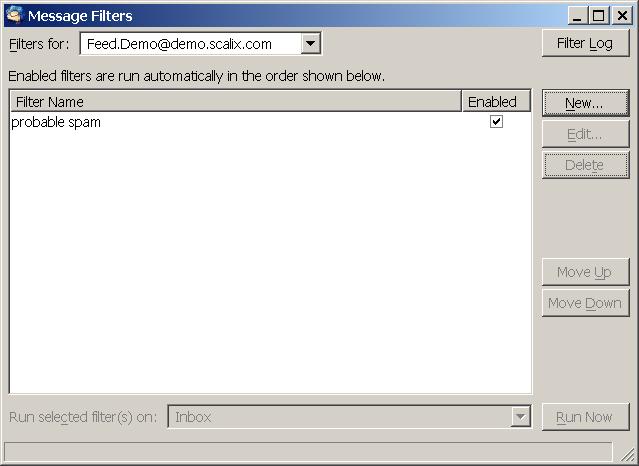
Then select the Message Filters entry from the Tools Menu:
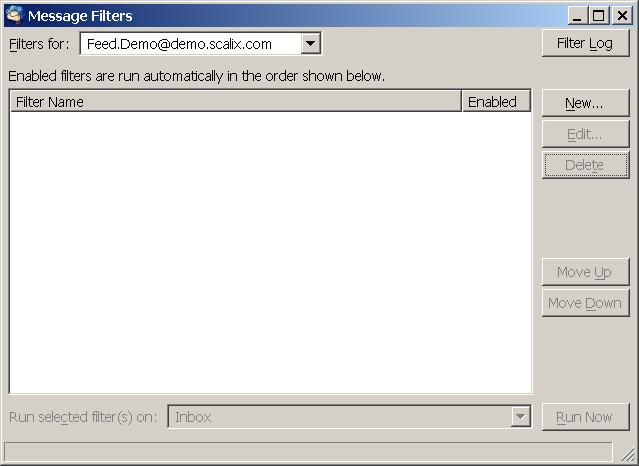
In the Message Filters dialog select New:
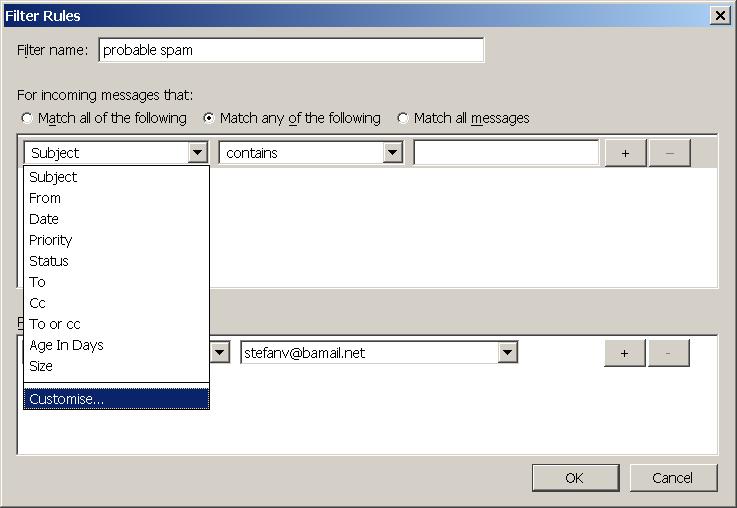
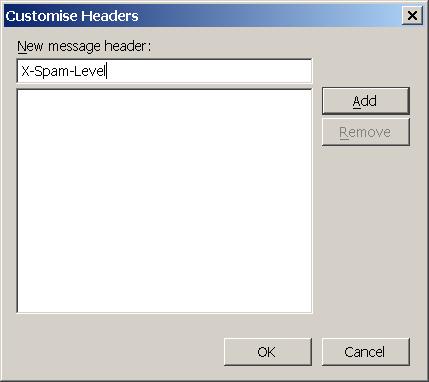
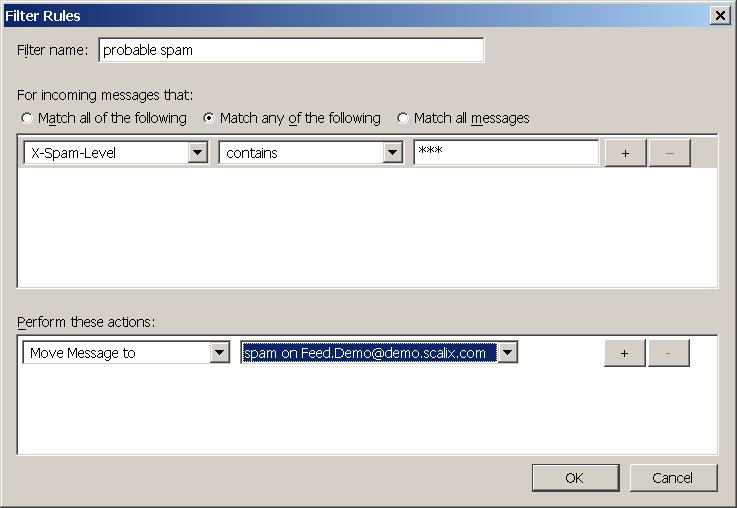
Enter a name for the filter, for example probably spam. If you have not yet done so you need to create a custom header. Select the left drop down list and choose Customise
Under New message header enter
X-Spam-Level
click Add:
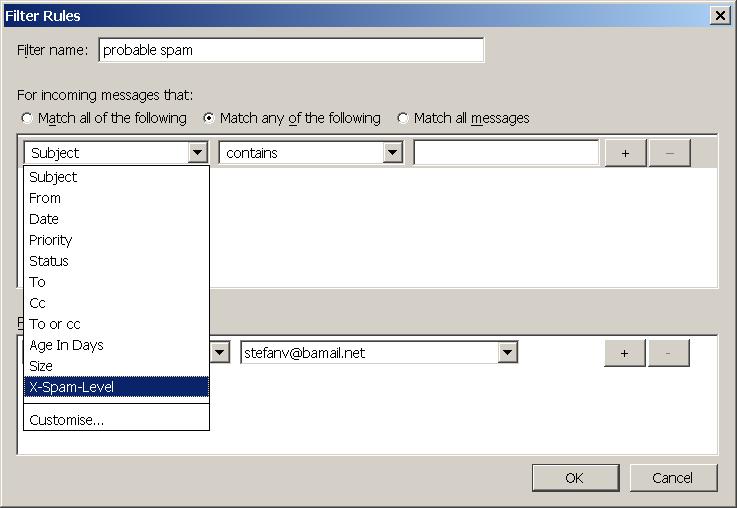
and then Ok. Select the newly created X-Spam-Level Header for the drop down list:
Select the earlier created spam folder as destination:
and enter three stars
***
into the textbox next to contains:
After clicking on OK you should end up with a newly created rule:
You can close the message filter dialog now.
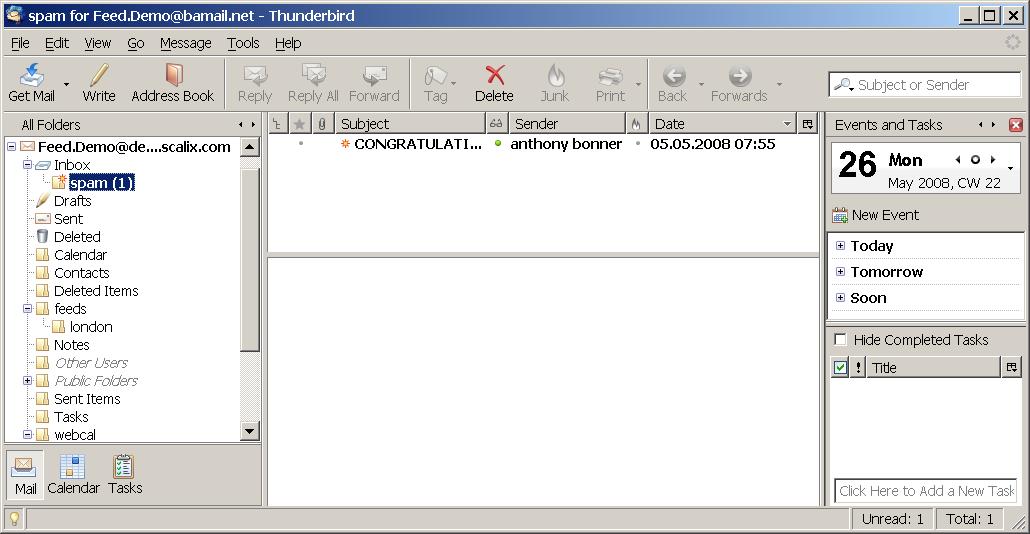
New spam will be moved to the created spam folder:
Customize Scalix AntiSpam and Scalix ZeroHour AntiVirus
The following sections describe how to customize the behaviour of Scalix AntiSpam and Scalix ZeroHour AntiVirus. Included there is a complete configuration example you can use if you decide that it meets your requirements.
The configuration file
Both Scalix AntiSpam and Scalix ZeroHour AntiVirus are configured in ~/sys/milter.cfg. The file consists of a group definition for Commtouch:
# group config for COMMTOUCH milter [COMMTOUCH]
A couple of global definitions
DEBUG_LEVEL=0 SOCKET_SPEC=local:~/temp/CTmilter_socket FNAME_TEMPLATE=~/temp/CTmilter.XXXXXX FEATURE_LEVEL=3 SX_REFID_HEADER=X-SMP-CT-RefID: %s SX_RCPT_HEADER=X-SMP-CT-Rcpt: %s
And the special stanzas for AntiSpam and AntiVirus which are described further down below.
To configure which types of content scanning to use change the FEATURE_LEVEL option to one of the following numbers:
| Level | Enabled Features |
|---|---|
| 0 | None |
| 1 | AntiSpam |
| 2 | AntiVirus |
| 3 | Both |
If for whatever reason you would want to disable Virus scanning you would need to set FEATURE_LEVEL to 1.
There should be no need to change any other global configuration parameters with the exception of DEBUG_LEVEL in case you want to turn on debug logging.
AntiSpam examples
Since level 0 is categorized as valid message simply accept it. The default action is to accept a message and you will not need to explicitly define this behavior but you can:
ACT_MSG_IF_AS_LEVEL_0=ACCEPT
Level one categorized mails are classified as not being spam. To add some headers so that users can filter mails using their client use the following example:
ACT_MSG_IF_AS_LEVEL_1=ACCEPT ADD_HDR_IF_AS_LEVEL_1=X-Spam-Flag: NO ADD_HDR_IF_AS_LEVEL_1=X-Spam-Level: * ADD_HDR_IF_AS_LEVEL_1=X-Spam-Status: No, score=1 required=3 tests=CommTouch
When you inspect the source of a message classified as level 1 you can see the added headers:
... X-Spam-Flag: NO X-Spam-Level: * X-Spam-Status: No, score=1 required=3 tests=CommTouch ...
Mails falling into the level 2 category are probably not spam. The following example is similar to the level 1 configuration above, with X-Spam-Level changed to two stars and the score of X-Spam-Status to two:
ACT_MSG_IF_AS_LEVEL_2=ACCEPT ADD_HDR_IF_AS_LEVEL_2=X-Spam-Flag: NO ADD_HDR_IF_AS_LEVEL_2=X-Spam-Level: ** ADD_HDR_IF_AS_LEVEL_2=X-Spam-Status: No, score=2 required=3 tests=CommTouch
The next example will accept Level 3 spam mails but tag them as spam through a header:
ACT_MSG_IF_AS_LEVEL_3=ACCEPT ADD_HDR_IF_AS_LEVEL_3=X-Spam-Flag: YES ADD_HDR_IF_AS_LEVEL_3=X-Spam-Level: *** ADD_HDR_IF_AS_LEVEL_3=X-Spam-Status: Yes, score=3 required=3 tests=CommTouch
You can extend the above example to include subject rewriting, e.g. prepend ***spam** to it:
ACT_MSG_IF_AS_LEVEL_3=ACCEPT ADD_HDR_IF_AS_LEVEL_3=X-Spam-Flag: YES ADD_HDR_IF_AS_LEVEL_3=X-Spam-Level: *** ADD_HDR_IF_AS_LEVEL_3=X-Spam-Status: Yes, score=3 required=3 tests=CommTouch CHG_HDR_IF_AS_LEVEL_3=Subject: ***spam*** %s
Please note that the placeholder %s will be replaced by the encoded original subject. In case the subject was encoded in something like UTF-8 you will end up with a garbled subject.
To temporarily fail the message and let the sending side try again later simply use:
ACT_MSG_IF_AS_LEVEL_3=TEMPFAIL
Reject all Messages categorized as Level 4 spam but save them to a file for later inspection:
ACT_MSG_IF_AS_LEVEL_4=REJECT SAV_DAT_IF_AS_LEVEL_4=~/spam/CTmilter.XXXXXX
Please make sure that the folder specified, ~/spam in the above example, exists and belongs to user and group Scalix. Also note that you will need to wipe out old files, etc. by yourself, as Scalix housekeeping scripts will not touch it.
Or to collect all spam messages of Level 4 in a special account:
ACT_MSG_IF_AS_LEVEL_4=ACCEPT REP_RCP_IF_AS_LEVEL_4=spam@demo.scalix.com
To simply discard a Level 4 spam message use:
ACT_MSG_IF_AS_LEVEL_4=DISCARD
AntiVirus Examples
To accept messages categorized as AntiVirus Level 2 but to also sent them to a special account use:
ACT_MSG_IF_AV_LEVEL_2=ACCEPT ADD_RCP_IF_AV_LEVEL_2=virus@demo.scalix.com
To reject level 4 AntiVirus messages use:
# antivirus level 4: virus ACT_MSG_IF_AV_LEVEL_4=REJECT
If you also want to save the message for later inspection use:
ACT_MSG_IF_AV_LEVEL_4=REJECT SAV_DAT_IF_AV_LEVEL_4=~/virus/CTmilter.XXXXXX
Please make sure that the folder specified, ~/virus in the above example, exists and belongs to user and group scalix. Also note that you will need to wipe out old files, etc. by yourself, as Scalix housekeeping scripts will not touch it.
Complete configuration example
The following is a complete configuration example with the following features:
- Debug logging off
- AntiSpam and AntiVirus enabled
- Accept AntiSpam Level 0
- Accept AntiSpam Level 1 and 2, but add headers
- Tempfail AntiSpam Level 3
- Reject AntiSpam Level 4
- Accept AntiVirus Level 0, 1 and 2, but add headers
- Tempfail AntiVirus Level 3
- Reject AntiVirus Level 4
# global config DEBUG_LEVEL=0 SOCKET_SPEC=local:~/temp/CTmilter_socket FNAME_TEMPLATE=~/temp/CTmilter.XXXXXX FEATURE_LEVEL=3 SX_REFID_HEADER=X-SMP-CT-RefID: %s SX_RCPT_HEADER=X-SMP-CT-Rcpt: %s # antispam level 0: definitely no spam # => accept ACT_MSG_IF_AS_LEVEL_0=ACCEPT # antispam level 1: no spam # - add headers # => accept ACT_MSG_IF_AS_LEVEL_1=ACCEPT ADD_HDR_IF_AS_LEVEL_1=X-Spam-Flag: No ADD_HDR_IF_AS_LEVEL_1=X-Spam-Level: * ADD_HDR_IF_AS_LEVEL_1=X-Spam-Status: No, score=1 required=3 tests=CommTouch # antispam level 2: probably no spam # - add headers # => accept ACT_MSG_IF_AS_LEVEL_2=ACCEPT ADD_HDR_IF_AS_LEVEL_2=X-Spam-Flag: No ADD_HDR_IF_AS_LEVEL_2=X-Spam-Level: ** ADD_HDR_IF_AS_LEVEL_2=X-Spam-Status: No, score=2 required=3 tests=CommTouch # antispam level 3: probably spam # => tempfail ACT_MSG_IF_AS_LEVEL_3=TEMPFAIL # antispam level 4: spam # => reject ACT_MSG_IF_AS_LEVEL_4=REJECT # antivirus level 0: definitely no virus ACT_MSG_IF_AV_LEVEL_0=ACCEPT ADD_HDR_IF_AV_LEVEL_0=X-SMP-CT-Virus-Status: No, score=0 required=3 tests=Commtouch # antivirus level 1: no virus ACT_MSG_IF_AV_LEVEL_1=ACCEPT ADD_HDR_IF_AV_LEVEL_1=X-SMP-CT-Virus-Status: No, score=1 required=3 tests=Commtouch # antivirus level 2: probably no virus ACT_MSG_IF_AV_LEVEL_2=ACCEPT ADD_HDR_IF_AV_LEVEL_2=X-SMP-CT-Virus-Status: No, score=2 required=3 tests=Commtouch # antivirus level 3: probably virus ACT_MSG_IF_AV_LEVEL_3=TEMPFAIL # antivirus level 4: virus ACT_MSG_IF_AV_LEVEL_4=REJECT
Troubleshooting
It is recommended that before you try out any hints given in this section you check that you have a valid license providing AntiSpam and/or AntiVirus abilities.
Known Issues
The sxmilter binary allows you to report back False Positives/Negatives when used in tool mode (refer to man sxmilter for details). As of now this will in case of False Positives only send back the message if the level is found to be 4. Messages categorized 3 or lower will not be sent back. Use the process described under How to manually report a false negative/positive instead.
How do I determine if I have a valid license
Scalix 12 and later
You need a license with one or both of the following options listed:
| Name=SMP_AntiSpam_CT | for Anti-Spam support |
| Name=SMP_ZeroHourAV_CT | for Zero-Hour Virus protection |
To check the available features for your license run sxlicense and refer to the Option: part of the output.
$ sxlicense Scalix License Status License Type: Temporary Key Type: Scalix Standard System Class: Multi-Server Domain: demo.scalix.com ID: 5361 LVID: 2016-10-17 Expiration: 2016-10-17 Standard Users: unlimited Features: TNEF WIRELESS MIGRATION HIGH_AVAILABILITY MULTI_INSTANCE MULTI_SERVER RECOVERY_FOLDER ARCHIVER Option: Name=SMP_AntiSpam_CT;Expiry=2016-10-17;GenericUsers=60 Option: Name=SMP_ZeroHourAV_CT;Expiry=2016-09-17;GenericUsers=60 License File: /var/opt/scalix/do/s/LicenseKeys/temporary.lic License Fingerprint (MD5): D8:AE:BB:F4:8F:1D:B9:9D:FB:E0:2F:A3:B6:D8:A4:1D
Scalix 12
You need a license with one or both of the following features listed:
| SMP_ANTISPAM_CT | for Anti-Spam support |
| SMP_ZEROHOURAV_CT | for Zero-Hour Virus protection |
To check the available features for your license run sxlicense and refer to the Features: part of the output.
$ sxlicense Scalix License Status License Type: Permanent Key Type: Scalix Standard System Class: Multi-Server Domain: demo.scalix.com ID: 42 LVID: 2016-05-31 Premium Users: 50 Standard Users: unlimited Features: TNEF WIRELESS MIGRATION HIGH_AVAILABILITY MULTI_INSTANCE MULTI_SERVER RECOVERY_FOLDER SMP_ANTISPAM_CT SMP_ZEROHOURAV_CT ARCHIVER License File: /var/opt/scalix/do/s/LicenseKeys/permanent.lic License Fingerprint (MD5): E5:4A:E5:25:27:D8:EC:CE:2F:48:9E:AC:09:0A:AF:0C
Please note that these license keys are no longer available as of July, 1st, 2008. All customers wanting to install either of the product options or updating their license after this date will have to upgrade their Scalix installation to 12 or higher.
Checking that the submission port is open
You can check that the submission port is open with the help of netstat:
# netstat -anpt | grep LISTEN | grep omsmtpd tcp 0 0 0.0.0.0:587 0.0.0.0:* LISTEN 15256/omsmtpd SUBMI tcp 0 0 192.168.220.3:25 0.0.0.0:* LISTEN 15250/omsmtpd SMTP
If the port is not open please check your smtpd.cfg and be sure to restart the relay after changing smtpd.cfg.
You can also use telnet to check that the relay is listening on the submission port:
$ telnet demo.scalix.com 587 Trying 192.168.220.3... Connected to demo.scalix.com (192.168.220.3). Escape character is '^]'. 220 demo.scalix.com ESMTP 11.4.0.11656; Sun, 20 Apr 2008 21:54:34 +0200 (CEST)
Test that the submission port is used for SWA/Platform/SSMTP
Refer to the table below and use the respective client to send an internal test mail.
| Component | Client |
|---|---|
| SWA | Scalix Web Access |
| SSMTP | Thunderbird configured to use SSMTP |
Then analyze the mail as described under How do I check if mails are (not) scanned.
How do I check if mails are (not) scanned
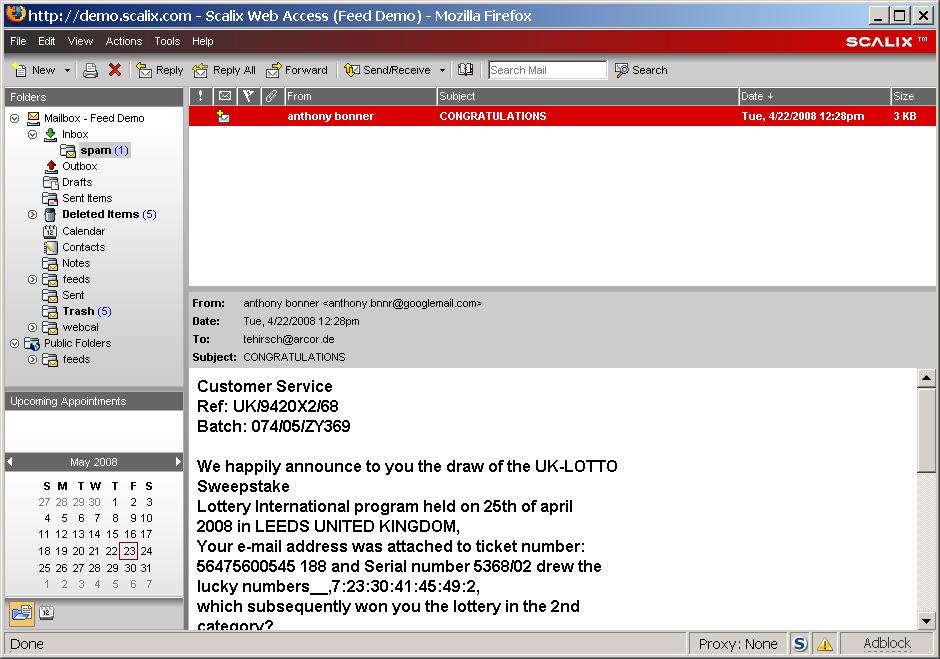
By looking at a message's headers you can find out if it has been processed by Commtouch or not. A scanned mail will always contain a RefID Header, an unscanned message not. The following example has been scanned as there is a RefID header present:
To: Feed Demo <Feed.Demo@demo.scalix.com>
Message-ID: <13928.10001208793135.demo.scalix.com@MHS>
Subject: test Mon, 21 Apr 2016 17:52:15 +0200
X-Mailer: swaks v20061116.0 jetmore.org/john/code/#swaks
X-SMP-CT-RefID: str=0001.0A0B0202.4832C20D.0082,ss=1,fgs=0
MIME-Version: 1.0
Content-Type: text/plain;
charset="US-ASCII"
Content-Transfer-Encoding: quoted-printable
Content-Disposition: inline
I can not see the sxmilter service
You need to have a valid license to use Scalix AntiSpam and Scalix ZeroHour AntiVirus. If you do not have a valid license you will not be able to see the Milter Server.
If you have a valid license you are able to see the MILTER Service when running omstat:
$ omstat -a | grep Milter Milter Server Started 06:29:43
Checking that sxmilter is running
You can check if sxmilter is running by executing
$ omstat -a | grep Milter Milter Server Started 10:21:56
or through ps
$ ps fax | grep sxmilter 21032 ? SNsl 0:00 sxmilter COMMTOUCH
or through omrc
omrc | grep milter scalix 21032 1 0 06:29 ? SNsl 0:00 sxmilter COMMTOUCH
The first parameter displayed for sxmilter in the process list will be the group name you chose in ~/sys/milter.cfg:
# group config for COMMTOUCH milter [COMMTOUCH]
New audit events
The following new audit events have been introduced:
| Name | Level | Description |
|---|---|---|
| milter-start | 9 | Relay is about to pass details of the message on to the milter |
| milter-end | 9 | Milter has passed the final results back to the relay |
| milter-add-rcpt | 11 | Relay has added a recipient as requested by milter |
| milter-del-rcpt | 11 | Relay has deleted a recipient as requested by milter |
To retrieve the current configured audit level for the relay use:
$ omshowaud -a | grep SMTP SMTP Relay 0
To enable logging of milter-start and milter-end events raise the level to 9:
$ omconfaud -a smtpd 9 omconfaud : Logging level updated OK. $ omshowaud -a | grep SMTP SMTP Relay 9
You need to restart the relay to activate the changed audit level. To immediately restart it use:
$ omoff -d 0 smtpd Disabling 1 subsystem(s). $ omon smtpd Enabling 1 subsystem(s).
The audit log information will be written to ~/log/audit. Below is an example with the above settings:
SMTP-Relay time 1208792837 Mon Apr 21 17:47:17 2016 +120 originator stefan.voelkel@demo.scalix.com milter-start name=CTmilter;time=1208792837;state=accept milter-end name=CTmilter;time=1208792837;state=accept recipient Feed.Demo@demo.scalix.com mta-message-id 12526.10001208792837.demo.scalix.com message-size 498 hop-count 0 summary-target U
To enable the milter-add-rcpt and milter-del-rcpt events you will need to increase the level to 11:
$ omconfaud -a smtpd 11 omconfaud : Logging level updated OK.
After restarting the relay you can find the modification events in the log file:
... milter-start name=CTmilter;time=1208793135;state=accept milter-add-rcpt name=CTmilter;time=1208793135;rcpt=stefan.voelkel@demo.scalix.com milter-end name=CTmilter;time=1208793135;state=accept ...
As with all other audit events, please refer to man omconfaud for further information.
Where to find log files
You can use omshowlog to access current log data.
To retrieve the current log level run
$ omshowlvl -a | grep Milter Milter Server 7
To alter the milter server log level to 9 use
$ omconflvl -a sxmilter 7 omconflvl : Logging level updated OK.
Please refer to man omconflvl for details on logging levels.
To enable MILTER API logging, set DEBUG_LEVEL in ~/sys/milter.cfg to 6 inside the group you want to enable logging for. Then stop sxmilter and run it in foreground.
To enable SMTPD logging use omshowlog, omshowlvl and omconflvl with smtpd as shown above.
To enable relay logs set DEBUG_LOG to TRUE in ~/sys/smtpd.cfg and check the file ~/tmp/smtpd-SMTP.log for Client Milter and Backend logging information. A successful startup with logging enabled may look like this:
[2016-04-20 17:13:48] Logging Started pid 28496 [2016-04-20 17:13:48] Cli 0/? milter->milter: OpenSession name 'CTmilter' path ' local:~/temp/CTmilter_socket' flag 'T' [2016-04-20 17:13:48] Cli 0/? milter->milter: Command2 cmd 'O' len 12 pnr 0 reply 'O' [2016-04-20 17:13:48] Cli 0/? milter->milter: Negotiate version 2 actions 31 protocols 0 [2016-04-20 17:13:48] Cli 0/? milter->milter: Negotiate reply 'O' result 0 [2016-04-20 17:13:48] Cli 0/? milter->milter: OpenSession result 1 [2016-04-20 17:13:48] Cli 0/? milter->milter: Command2 cmd 'Q' len 0 pnr -1 reply 'c' [2016-04-20 17:13:48] Cli 0/? milter->milter: Close reply 'c' result 0 [2016-04-20 17:13:48] Cli 0/? milter->milter: CloseSession result 1 [2016-04-20 17:13:48] Cli 0/? cfg->milter: AddToMilterList result 1 [2016-04-20 17:13:48] SMTP Relay 11.4.0.11641 started (28496): Sun, 20 Apr 2008 17:13:48 +0200 (CEST) for SMTP
Besides the possibilities listed above you can also run sxmilter in the foreground by first stopping the service and then running it with the -i parameter:
$ omoff -d 0 "Milter Server" Disabling 1 subsystem(s). $ sxmilter -i
To run smtpd in foreground use
$ omoff -d 0 -a smtpd Disabling 1 subsystem(s). $ omsmtpd -i
Received: header logging
sxmilter will log host and IP information at level 13. Use these commands to acivate and examine this log information:
$ omconflvl -a sxmilter 13 $ omshowlog -s sxmilter -l 13
omshowlog shows "MILTER: milter_eomActions: mkstemp failed"
Make sure the directory specified in the SAV_DAT_IF_AS_LEVEL_N options located in ~/sys/milter.cfg exists. With the following setting in milter.cfg:
SAV_DAT_IF_AS_LEVEL_4=~/spam/CTmilter.XXXXXX
Messages categorized SPAM level 4 would be created in the directory spam located in the server's home directory. Depending on your installation the path to the server's home may vary, but will look something like this:
/var/opt/scalix/do/s/spam
With the above settings a possible filename for a spam message would be:
/var/opt/scalix/do/s/spam/CTmilter.52xVgi
Make sure that the user scalix has write permissions in this folder. To setup the above example you could use the following commands:
$ mkdir /var/opt/scalix/do/s/spam $ chown scalix:scalix /var/opt/scalix/do/s/spam
Please keep in mind that you need to take care of cleaning out these directories, as Scalix housekeeping scripts will not touch them.
Implementation Details
To improve the relay's throughput and to adapt to the blocking nature of milter calls the default configuration of the number of relay processes has been changed. Up to Scalix 11.3 there were 6 relay processes, each handling a maximum of 16 concurrent connections. Starting with Scalix 11.4 there will be 16 processes, each handling a maximum of 6 concurrent connections.
A new MILTER interface has been implemented in the Scalix SMTP Relay. The Commtouch service is integrated through this new MILTER interface by wrapping Commtouch's scanning engine ctengine. For more information on MILTERs please refer to http://www.sendmail.com/sm/open_source/download/
Please be advised that the option SMTPFILTER has been deprecated in favor of SMTPMILTER, and should not be used any longer.
The Commtouch MILTER will be run by the new sxmilter service.
All existing Relay rules in smtpd.cfg will be applied exactly once before the messages gets processed by any configured milters. Unlike sendmail Scalix will call milters sequentially and not in parallel to avoid conflicting changes to headers by multiple milters.
A message will only be accepted if all configured milters return the ACCEPT action. As soon as one returns with an action different than ACCEPT (e.g. DISCARD, TEMPFAIL, ...) processing stops, the later milters will not be called and the last action returned will be applied to the message.
When a message has been processed by Scalix AntiSpam or Scalix ZeroHour AntiVirus a special header, by default called X-SMP-CT-RefID, will have been added to it. This header is used to identify the message when reporting false positives/negatives.
The newly implemented MILTER interface can also be used to integrate other applications like Spamassassin, AMaViS or ClamAV through their respective milters. Be advised that this has not been tested by Scalix.
The provided MILTER for Commtouch ctengine integration is intended to be used with Scalix only, no tests have been made to ensure sendmail compatibility.
Scalix is compatible to version 2 milters.
It is possible to prefix the subject of a spam message with something like "***SPAM***", but this will ignore the subjects encoding and might break the display of some character sets.
When saving the message to a file the original message will be saved. In case you are replacing recipients for this message they will be added as special headers.
When discarding or rejecting a message you can not replace the recipients, since the message will not be delivered to users on your system. You can however save the message to a file for later inspection.
Supported MILTER features
The following features are supported:
| Header | add, insert or change headers |
| Rcpt | add or delete recipients |
| Action | accept, reject, discard or tempfail message |
Additionally the following feature is supported by the relay, but not by the Commtouch milter:
| Body | replace original body with something else |
It can be used in combination with other milters though.
Unsupported MILTER features
| Change 'from' | Not supported by Scalix 11.4 |
| Quarantine action | At this point we do not support the quarantine message action, as a workaround you may want to consider replacing the recipient instead. |
| Extended recipients | When adding or deleting recipients you can not use "First Last <first.last@scalix.com>" only plain email addresses are supported e.g. "first.last@scalix.com". |
| Symbol list | You can not pass sendmail macros to the milter. |
| Reply with code and text | You can not customize the reply code and text, e.g. "441 tempfail by milter X for reason Y" is not possible. |
Milter configuration options
You can alter several parameters influencing milter behavior in timeout situations[1]:
INPUT_MAIL_FILTER=('CTmilter', 'S=local:~/temp/CTmilter_socket, F=T, T=C:300s;S:10s;R:10s;E:300s')
The three parameters passed to the milter are
| Name | Meaning |
|---|---|
| S | Location of the socket to talk to |
| F | What to do if the milter is unavailable (must be F=T) |
| T | Timeout parameters |
Please note that unlike sendmail Scalix only supports tempfailing a message when the milter is unavailable (F=T) because at the time the milters are processed the connection has already been accepted.
The timeout parameter is composed by the following flags separated by semicolon and postfixed by either s for seconds or m for minutes:
| Flag | Meaning |
|---|---|
| C | Timeout for connecting to a filter. If set to 0, the system's connect(2) timeout will be used. Default: 5m |
| S | Timeout for sending information from the MTA to a filter. Default: 10s |
| R | Timeout for reading reply from the filter. Default: 10s |
| E | Overall timeout between sending end-of-message to filter and waiting for the final acknowledgment. Default: 5m |
In this example
INPUT_MAIL_FILTER=('CTmilter', 'S=local:~/temp/CTmilter_socket, F=T, T=C:5s;S:10s;R:15s;E:20s')
the message will be tempfailed if any of the following is true:
- connecting to the milter takes longer than 5 seconds
- writing the message to the milter takes longer than 10 seconds
- reading the reply from the milter takes longer that 15 seconds
- the whole operation takes longer than 20 seconds
Please note that changing the timeout values can have severe impacts on your system. Do not change these values without fully understanding the consequences.
Message Path if SMTPMILTER is set to TRUE
- Client->Milter: cache msg up to the last dot before reply
- Milter->Milter: call 1st milter to process the cached msg
- Handle msg modification from 1st milter (or msg action)
- Repeat step 2 and 3 for Nth milter using modified msg
- Milter->Backend: handle msg action and reply to Client
- ACCEPT: start backend (unix.in) and send the modified msg, then reply back to Client with 2xx if OK (or unix.in error if not OK)
- REJECT: drop the msg, reply back to Client with 5xx
- DISCARD: drop the msg, reply back to Client with 2xx
- TEMPFAIL: drop the msg, reply back to Client with 4xx